The lab that I have used to exploit is a TryHackMe lab under network services 2 module explaining about the NFS enumeration and exploitation.
Network File System and
allows a system to share directories and files with others over a network. By
using NFS, users and programs can access files on remote systems almost as if
they were local files. It does this by mounting all, or a portion of a file
system on a server. The portion of the file system that
is mounted can be accessed by clients with whatever privileges are
assigned to each file.
·
The client will
request to mount a directory from a remote host on a local directory just the
same way it can mount a physical device.
·
The server
checks if the user has permission to mount whatever directory has been
requested. It will then return a file handle which uniquely identifies each
file and directory that is on the server.
If someone wants to access a file using NFS, an
RPC call is placed to NFSD (the NFS daemon) on the server. This call takes
parameters such as:
- The file handle
- The name of the file to be accessed
- The user's, user ID
- The user's group ID
Enumeration
The first step of enumeration is to conduct a port scan, to find out as much information as you can about the services, open ports and operating system of the target machine. You can go as in-depth as you like on this, however, I suggest using nmap with the -A and -p- tags.
The following screenshot
provides the nmap scan on the IP and the services associated with it.
Your client’s system needs a
directory where all the content shared by the host server in the export folder
can be accessed. You can create this folder anywhere on your system.
sudo mount -t
nfs IP:share /tmp/mount -nolock
|
Tags |
Function |
|
Sudo |
Run as root |
|
mount |
Execute mount command |
|
-t nfs |
Type of device to mount is nfs |
|
IP:Share |
IP address of the NFs server |
|
-nolock |
Not to use NFS login |
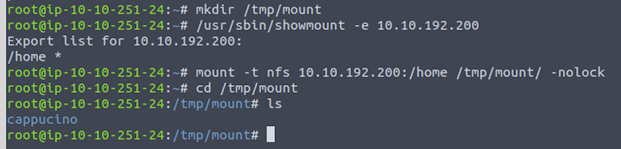
The following screenshot
provides the present visible share drive.
The following screenshot
provides the user nfs server mounting and after this we will be able to access
the data from the NFS server.
Exploitation
NFS shares- Root Squashing
is enabled and prevents anyone connecting to the NFS share from having root
access to the NFS volume. Remote root users are assigned a user “nfsnobody”
when connected, which has the least local privileges.
SUID means that the file or
files can be run with the permissions of the file(s) owner/group. In this case,
as the super-user. We can leverage this to get a shell with these privileges!
The bash script to exploit
the NFS server is here
The pathway to exploit is provided below
- NFS Access
- Gain Low Privilege Shell
- Upload Bash Executable to the NFS share
- Set SUID Permissions Through NFS Due to Misconfigured Root Squash
- Login through SSH
- Execute SUID Bit Bash Executable
- ROOT ACCESS
Let’s do this!
NFS Access
The following screenshot
provides the information about sensitive data present on the file share ssh
access permission files.
Gain low Privilege
The following screenshot
provides the lower access to the NFS
The following screenshot
provides that the access creds for the ssh is copied to the local system
Upload Bash Executable to the
NFS share
The following screenshot
provides that the bash file is loaded into the mounted NFS folder
Set SUID Permissions Through
NFS Due to Misconfigured Root Squash
The following screenshot
provides the SUID permissions are set on the bash files due to misconfigured
root squash which makes the file executable by group and owner users
Login through SSH
Login to the server using the ssh pem files
Execute the bash file and
access the root.txt file to get the flag













Need for Speed!! Baby .. nice 1
ReplyDeleteha ha!!
Delete